Enhancing Cyber Security with SSL Technology
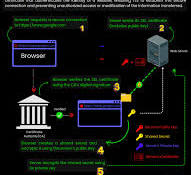
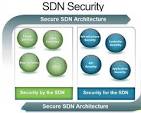
The Importance of SSL in Cyber Security In today’s digital age, where cyber threats are constantly evolving and becoming more sophisticated, the need for robust security measures has never been greater. One crucial component of ensuring secure online communication is the implementation of SSL (Secure Sockets Layer) technology. SSL is a protocol that encrypts data […]
Read More →